Increase velocity and reduce technical debt through our code review service
Software Testing ServicesAdd Quality To Your Product, Boost Your Confidence.
As a Software Testing Partner, we analyze, plan and research your requirement. Customer-centric approach with 100% success.
Source Code Review (SCR) is a systematic & Security examination of the Source Code of Application and Software. It looks for Security Loop Holes, Bugs that may have been planted and overlooked during Application and software development.
Sometimes, certain Application and Software may contain vulnerabilities which can aid attackers to extract vital information and may lead to loss of intellectual property & Secure Data. Reviewing Source Code helps to verify the implementation of key security controls. It also looks for design flaws and discovers hidden vulnerabilities in any application and software.
Source code analysis not only distinguishes which proclamation on which line of code is helpless, but at the same time can recognize the polluted variable that represents the vulnerability. Along these lines it represents the spread from underlying driver, to final product. This furnishes application developers with a conclusion to end outline of each example of vulnerability, enabling them to rapidly comprehend the idea of the issue. Also check the source code analysis tool.
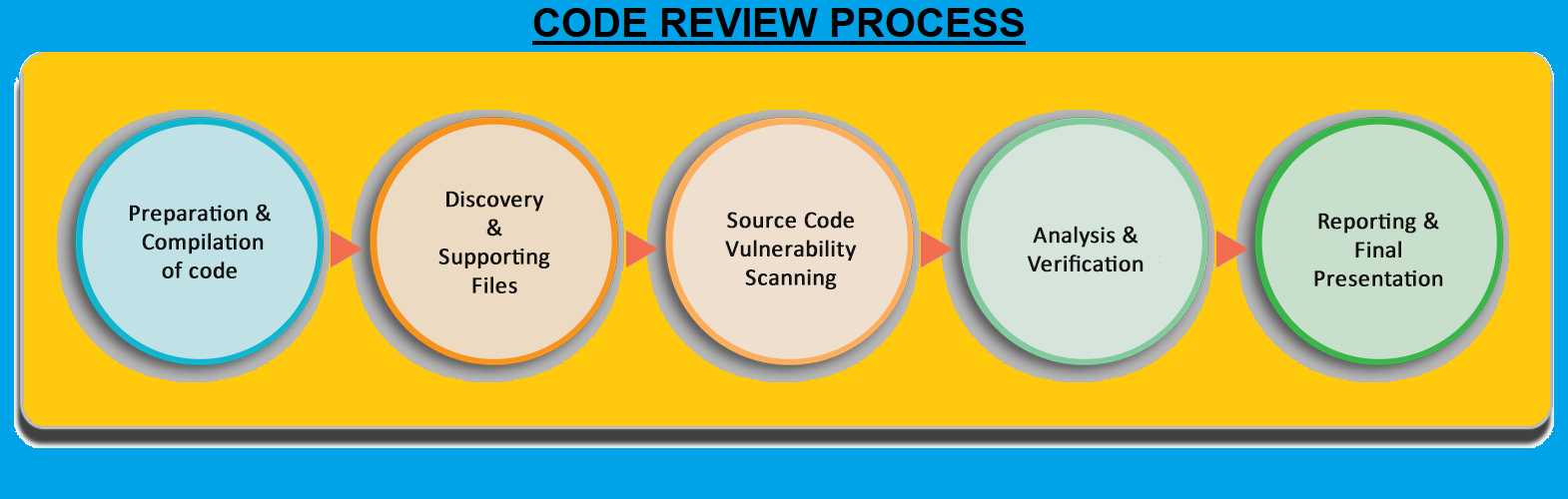
What is Source Code Review
Source Code review discovers hidden vulnerabilities, design flaws, and verifies if key security controls are implemented. Many a time software and applications contain bugs and vulnerabilities, which creates the possibility that the product might face potential attacks from attackers trying to take advantage from such flaws. This can give attackers with an inside view of important information (data Leakage) and assets.
Many a times the development and deployment phase of an application is hurried upon for swift completion of project. In such situations, there remains high possibility that the product might not be put through proper security tests. As a result clients using those products are more likely to fall victim to attackers. Such applications should be passed through rigorous review process (Vulnerability Assessment) to detect the vulnerabilities, present in them.
Source Code review : Approach
The following steps are identified with the procedure involved:
• Source Code Review starts with review of the software, and the coding process that went into making the software. The process includes discussion pertaining to the software, with the development team. The developers are required to respond to an extensive list of questions related to security for the purpose of identifying security design issues.
• The second step involves preparation of a code review plan.
• The third step involves identifying comprosing data placed within the code. Another important task is to find bad coding techniques which makes it easier for attackers to gain access to a software.
• Upon completion of analysis, the next step involves the verification of existing flaws. Every possible security vulnerabilities is listed and remedial steps introduced to improve the development process that a software goes through.
The exhaustive process of finding bugs through Source Code review helps to detect the vulnerable line of code. Upon doing so, it exposes the root of the problem. This gives the Application Developers a complete general idea of each occurrence of susceptibility, allowing them to swiftly comprehend the temperament of the hitch.
After completion of code review we’ll provide you with a complete details of cyber security vulnerabilities as well as suggestions to improve overall development process.
Source Code Review – Challenges
Since applications contain bugs; there is a chance that an attacker may have the capacity to abuse some of them to effect or access your information resources and abilities. Web applications specifically are more be influenced by these vulnerabilities, as they are much of the time created and sent rapidly underway in brief terms without adequate time spent in security testing. We have a thorough system for auditing web application code. Our survey procedure is particularly custom fitted to discover vulnerabilities that ordinarily happen in applications. We utilize a blend of both computerized and manual strategies to lead a source code survey. Using tools, for example, Checkmarx and Fortify, we can get vulnerabilities crosswise over expansive code-bases, and then limited our concentration onto security-particular modules of code, (for example, those actualizing encryption or approval) and additionally check for business rationale issues.
How we can Help You
Applications and software should be put through Source Code Reviews even as early as during the initial phase of project development. Experts at ELAARSON stress upon the importance of performing such Reviews right from the early stages of project development. It is because the expenses conjured during the development stage of a software is less as compared to deployment or implementation phase of the product. Source Code Reviews can be done both on site and remotely, according to the convenience of the client. We are among the top rated Code Review Company in India.
Hybrid Approach
DevOps / Development Integration
Remediation Advice
Request Pilot Project Terms & Condition Privacy Policy
Copyright © ELAARSON Industries 2019 - 2026. All rights reserved.